-
6 months after fixing Internet woes
About 6 months ago, I wrote about how I replaced all of my dad's networking gear with Ubiquiti products including the USG
, Cloud Key
, and a pair of UAP-AC-LR
s. While it didn't completely cure his Internet issues, we were at least sure that the router and access points weren't the problem. His cable provider kept doing work on the connection and eventually he replaced the cable modem with an ARRIS 6183
. I don't believe that the cable modem was the problem, but I wasn't going to argue with it working (we had already swapped out the cable modem with a different SB 6141).
The gear has been rock solid; one of the access points wasn't touched since the day we installed it; the USG was rebooted when the cable modem was replaced and my dad had to reset the other AP when he did some wiring changes in a closet.
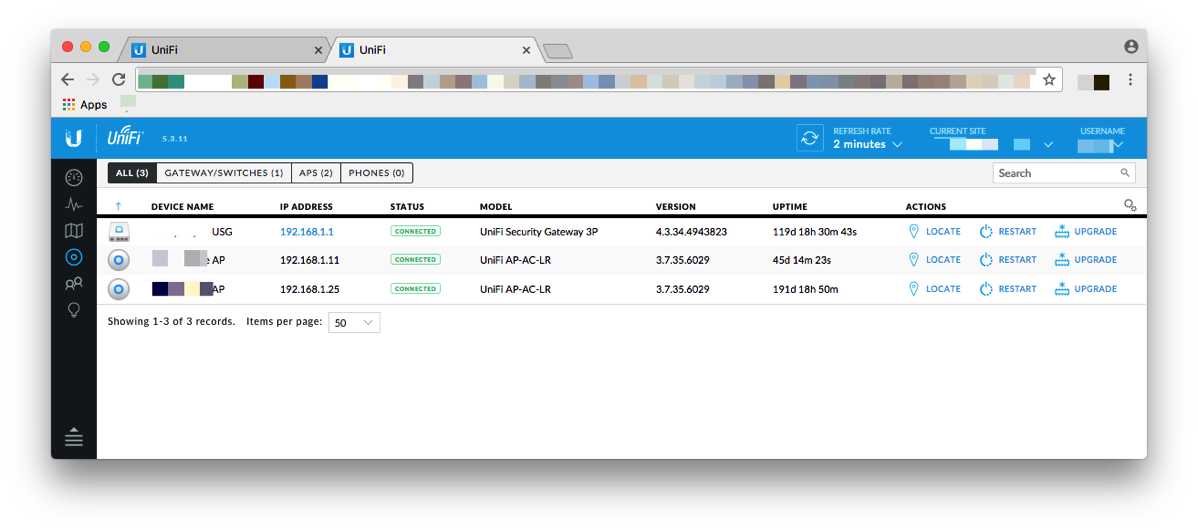
Ubiquiti has been putting out regular updates to the equipment, but I decided to just leave it on older versions as everything was running. Yesterday I went ahead and performed the upgrade remotely which was quite scary as any firmware upgrade could render a device useless. Luckily upgrading all components went smoothly; the Cloud Key took a little longer than expected and I almost panicked when it didn't come back online.
I asked my dad if he's had any problems with the Internet and he said no; this was news to my ears. Prior to installing the Ubiquiti equipment, the family's solution for any time they had a problem was to reboot the cable modem and router. This no longer happens and everything just works.
As much as I'd like to recommend this type of setup for the average household, the separate components make it intimidating. For anyone with a little networking knowledge that has to handle an Internet connection for someone else like a family member or a small business, I'm not sure that you can beat Ubiquiti for the features at the price point.
Yes, I know I sound like an advertisement, but the more I use their hardware, the more I keep looking at reasons to get more and see what it can do.
-
Making medical decisions based on cost
Throughout my career I have been fortunate enough to have good, company-sponsored health insurance and have been in relatively good health. I only thought a little about healthcare costs when I was self-employed and we were on a continuation plan (sort of like COBRA). While the costs were not cheap, if I recall correctly around $1100 a month about a decade ago, we had good coverage and could see whatever doctor we wanted. When I lost my job last year I kept coverage through a COBRA plan until my new employer's plan started; they had a 60 day waiting period which is kind of brutal if you're trying to maintain continuous coverage.
When I picked a plan I picked what I thought was an okay plan: they had HRA plans which basically gave you a few hundred dollars to reimburse costs. It wasn't until I started looking at the cost of the ulcerative colitis medicine that I have been on for many years that the costs started to sink in; the medicine, Delzicol, was about $600 a month vs the $70 for a 3 month supply that I had previously. That adds up quickly. I was in the process of weaning myself off the medicine since I had been doing well for years so I didn't think much of it at the time. In addition to the medicine costs, the plan had a very high deductible and the doctors couldn't tell me how much a visit would be until I got the bill. It wasn't a regular PPO or HMO plan with a fixed fee for a doctor's visit and the cost sharing didn't kick in until I hit the deductible; the bill from a doctor was whatever negotiated rate the doctor would accept.
In November when I decided to become self-employed again I went on a COBRA plan through my old employer. Now I had to pay the full cost of the mediocre plan which amounted to over $1500 a month. While expensive, it was a lot better than having no coverage at all and luckily I can afford this.
About 2 months ago due to an issue with a client I had a lot of stress. Stress typically causes my colitis to flare up and this time it was a doozie. I resisted seeing a doctor but needed help. I went to see a physician's assistant (they can prescribe medications which is good) and while discussing my condition with her and treatment options I was using the CVS/Caremark app to see how much each medication would cost. I shouldn't have to put a price on my health but high costs would increase my stress and lead to a vicious cycle. One drug was $1000 a month, another was $500 a month so we settled on another drug where the cost was just under $100 for a 2 week treatment. She also recommended a colonoscopy, but I declined that as I suspect that would have been several thousand dollars.
Unfortunately the first medicine didn't work so we went with another drug. This one was going to cost close to $200, but it had to be done. However, I found an app called GoodRx that shows you prescription costs and has a drug discount card attached to it. Using this, I was able to reduce my cost by about $45. Yes, it would cost me more with insurance to get a prescription than without it. That didn't work either, so as a last resort we went with a drug I didn't want to take, but has been quite effective in the past; that prescription, with the discount card, was only $15. Luckily, it seems to have done the trick.
The good news for me is that we're changing insurance plans to one with more upfront pricing and hopefully more cost effective coverage. I'm also not going to rely on medicine alone to treat my colitis; I am embarking on a complete diet change (look for a future post about that) as I feel that there are potentially other treatment options for my condition.
I do feel fortunate that I can afford health insurance and out of pocket healthcare costs. This episode gave me a bit of a scare and really highlighted for me what some people have to struggle with due to the high costs of healthcare in our country; people shouldn't have to make healthcare decisions based on cost. Unless I misread something or my COBRA coverage was different than normal employees get, besides base cost, the insurance plan really had a lot to be desired.
-
Dongles everywhere!
In the last few revisions of the MacBook and MacBook Pro, Apple has replaced the legacy ports with USB-C ports which some think is forward thinking and others complain that their devices don't connect. Last fall, when the last MacBook Pros were announced, I was eyeing one, but ultimately decided against buying one. However, when Apple had a sale on the dongles to placate people, I thought about what I would need for my next computer. I bought a USB-C to Thunderbolt 2 adapter and a USB-C to USB-A adapter.
Fast forward to last month when Apple announced the 2017 MacBook Pros and I decided that it was time to replace my almost 5 year old MacBook Pro. I again, had the option to purchase dongles, but decided the 2 I had were all that I would need. My current setup is 2 27" Thunderbolt displays that each have 3 USB-A ports, FireWire 800 and a Thunderbolt port. With only the USB-C to Thunderbolt 2 adapter, I'm able to hook up my MacBook Pro to 1 display (second display is daisy chained) and all my devices work. When I travel, I can bring the USB-C to USB-A adapter in case I need to use a card reader.
While I may not be typical in my setup, basically 2 dongles are all I need to make my new computer hook up to all my legacy devices; this is really no big deal. Next year, however, when/if Apple releases its own displays again, they will unlikely have legacy ports. At that time, I'll get a few USB-C to USB-B cables for my scanner and hard drive dock and a few USB-C to USB-A adapters to hook my Lightning cables; total cost for all this will be maybe $30 and the cables/dongles will always be plugged into the display. Nothing to lose and a minor cost to move forward.
I'm not sure why there was so much uproar in the Mac community about getting rid of legacy ports; to me this is a much smaller deal (if any) than moving from 30 pin to Lightning because of the shear number of devices and cables I have lying around the house.
-
Review: ZTE Mobley
Several years ago, I worked for a company that sold Sprint service. As part of my job, a "perk" was a company issued phone and then when the MiFi mobile hotspot was released, I got one of them for experimentation and use. (I use perk lightly because having a company issued phone or device is more of a tether keeping you connected all the time.) When I left the company in 2010, my boss said that I could use the company discount to purchase a device and plan; I purchased a MiFi and had a $45/month plan for 5 GB of data. After about a year, I realized that I wasn't using the device much and cancelled the plan.
For the most part, I haven't had a need or desire for a mobile hotspot and my iPhone's mobile hotspot has worked fine when I needed it. Over the last year or so, I've heard advertisement after advertisement about "built in 4G/LTE" in cars which seemed like a way just to keep the kids in the back quiet and I ignored the ads. Earlier this year, I saw that AT&T was dropping the price of their "Connected Car" plans to $20/month for unlimited data (22 GB, in reality and then de-prioritization). Now things were starting to get interesting in pricing.
AT&T offered this plan on cars that had built in cellular, as well as with the ZTE Mobley which plugs into a car's OBD-II port. The only problem with this, for me, is that I have an Automatic plugged into the port and only being able to use the device in the car had limited utility. Luckily, I read on forums that people were buying adapters to plug it into USB or AC. Since the cables looked like someone hand made them, I decided to make my own so that I could choose the parts. I picked up an OBDII Connector Cable Pigtail
and a 5v to Dc 12v USB Converter
(I picked this one because any heat generated from the electronics wouldn't be right at the end of the cable). I soldered the pieces together and had a USB to OBD-II power cable.
I purchased the Mobley outright ($99) with no activation fee. When it arrived, I plugged it into my cable and into USB and it powered right up without problems. My first few uses of it were when I went to the car dealer and had to wait around; I plugged it into a USB battery (at peak power consumption, it uses something like 700 mW). It performed quite well and I got acceptable speeds without having to worry about jumping on an unknown WiFi network and dealing with my VPN.
The next test was when we drove about an hour to go camping; my wife was in the passenger seat and my son was in the back seat. My son had an iPad and was entertained for the trip. My wife started out the drive just saying that she would use her phone, but about 10 minutes down the road, she asked my son to hand up her iPad. From that point on, I think the hotspot gained a permanent place in our longer car rides! This past week we went on a driving vacation and covered about 1500 miles. The hotspot powered up when the car started (it was plugged into one of the USB ports; my car has 2 USB ports, but I bought a 2 port cigarette lighter to USB adapter, so I had a total of 4 ports) and was available wherever we had AT&T coverage which turned out to be maybe 75% of the total time in the car.
In one of the hotels we were staying, I was able to get over 20 Mbps down which to me is amazing considering my first cable modem was 5 Mbps down and the first cellular data links I worked with at QUALCOMM were 9.6 Kbps.
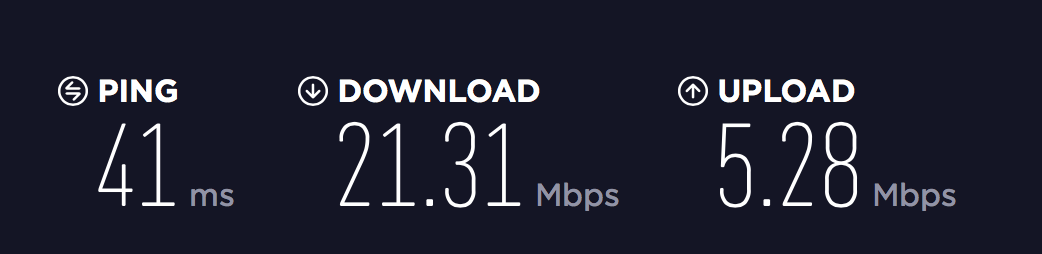
While $20/month seems like an unnecessary expense for times that I won't use it, I can justify the expense.
Pros
- Easy to use (just plug it in and connect to WiFi).
- Coverage wherever AT&T has coverage.
- Hard to use up 22 GB a month in normal usage (we used about 17 GB on our last trip and that was using it in the car and hotel).
- Device is reasonably priced ($99).
- Monthly fee is reasonable ($20/month).
- Automatically turns on when power is applied.
Cons
- Have to buy or make a cable to use outside of the car.
- Limited to 5 devices at a time. This seems like a lot of devices, but we had a total of 6 and some devices always stay connected to WiFi causing me to have to block/unblock a device).
- Doesn't support carrier aggregation which would support higher data rates.
Summary
As much as I didn't want to think that a mobile hotspot would fit into my usage, it has proven to be an excellent device. I'm sure that my review (except for the auto power on) would be the same with any mobile hotspot, but the price of the device and the price of this plan make the ZTE Mobley a keeper. Even though you can turn your phone into a hotspot, it doesn't stay on all the time and uses data from your plan. By having a separate device, you don't have to worry about going over your usage and being throttled and don't have to worry about turning on the hotspot.
I would be interested in trying out the other mobile hotspots that AT&T has to offer as they would look neater than my soldered set of cables and be more compact, but I have to check the terms and conditions to see if there is a problem moving my SIM to a different device and keeping the same plan.